Setting Up Windows 11 Enterprise LTSC VMs and Windows Server 2025 Domain Controller in Proxmox
I went to https://www.microsoft.com/en-us/evalcenter/evaluate-windows-11-enterprise and downloaded the LTSC version of Windows 11 Enterprise since what I am using these ISOs for is very short-lived and not wide in scope. I will be doing this on a server that I don’t believe has much power, even though my friend already in IT said it does. Now to create the VMs. I think maybe I’ll set up two for now. I will probably create a few more but not run them at the same time.
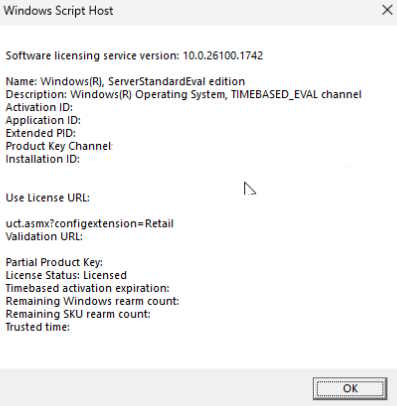
Before I went any further I wanted to find out how much time I had left on my evaluation of Windows Server. I have been running it for several months now, not even sure how many but I just assumed I was coming up on the end soon. Wouldn't have surprised me if I had a week left because it seemed like it was such a long time ago. But I looked up the command to find out how many days or minutes were remaining on my evaluation in windows server, I don't know if this works in other OS's but I entered:
slmgr /dlv
This command gave me the info:
I was told I had 181,899 minutes and 127 days left on the Windows Server evaluation. It also showed I had a remaining Windows rearm available. After looking into that, I found I can refresh the evaluation one time before needing to reinstall. That sounded like something I wanted to keep in mind.
I hadn’t uploaded the OS ISOs to Proxmox yet, so I went to the Proxmox web interface:
Datacenter > Proxmox node > Local (proxmox) storage (where OS images go) > ISO Templates > Upload > Select File > navigated to my file server to pick the ISOs.
It took quite a while, barely passing 6% after five minutes.
I first tried uploading the Windows 11 ISO via the Proxmox web interface, but it kept failing with error 0. Switching to SCP from my Windows laptop terminal to copy the ISO directly to the Proxmox server also failed, despite several tries.
I discovered my 256GB NVMe drive was partitioned by Proxmox with only about 68GB for root partition, which was almost full. Running df -h and du on Proxmox showed most root space was taken up by VM backups in /var/lib/vz/dump. Apparently, my recent work to protect the Windows Server evaluation from expiring caused this space issue.
I deleted older backups in /var/lib/vz/dump, keeping only the latest one, and adjusted Proxmox backup retention to keep just one backup going forward. This freed up significant space, and now I had plenty of room for uploading ISOs and creating VMs.
To check disk usage in /var/lib/vz and find largest folders:
du -h --max-depth=1 /var/lib/vz | sort -hr
To list backups sorted newest first:
ls -t /var/lib/vz/dump/
To delete all backups except the newest one:
ls -t /var/lib/vz/dump/vzdump-qemu-100-*.vma.zst | tail -n +2 | xargs -r rm -f
This command deletes all .vma.zst backup files except the latest.
I also learned how Proxmox splits storage between root and volume groups, and how VM disks, backups, ISOs, and system files are stored separately. This helped me understand why I thought I had enough space but actually ran out on root.
I retried uploading via the web interface, and this time it finished within a few minutes. Now I’m thinking about shrinking the thin provision size for my Windows Server VM since it’s currently 50GB and might not need that much. I thought I had 256GB total, but partitioning changes the available space significantly.
2025-06-10
Yesterday I spent hours trying to get the first Windows 11 VM to boot properly in Proxmox. I must’ve recreated the VM at least 15 times chasing the same errors. Every time I tried UEFI, I got the “BdsDe: failed to load Boot0002 UEFI EMU QEMU HARDDISK” error or similar boot failures. When I switched to SeaBIOS, I could reach the installer but setup complained about not meeting Windows 11 system requirements.
At first, I suspected specs—cores, RAM, or disk size—so I tested different virtual disk sizes: 30GB, 60GB, 64GB. I needed to keep drives small to fit multiple workstation VMs on my limited storage. The errors kept happening, and I started wondering if I really needed more than one VM.
I imagined a job interview: “Why do you want this job if you can do advanced work like this?” they’d ask. Then, “You mean you only added one VM?” Me, smiling, “Yep!” “Well, we’ll let you know… don’t call us, we’ll call you!”
I also experimented with many VM creation settings: toggling QEMU Agent, switching between SATA, IDE, SCSI, and VirtIO Block for system > Bus/Device, changing RAM. Nothing fixed it. I followed many instructions—some swore by VirtIO Block, ChatGPT by IDE, others recommended SCSI. I even mistakenly chose SATA once. None of these solved the two persistent errors blocking Windows install.
Each time I recreated the VM, I followed the same process:
Datacenter > my node > right-click > Create VM.
In the wizard, selected OVMF (UEFI) under System > BIOS and added TPM 2.0 support.
For storage controller, chose VirtIO SCSI single.
Mounted Windows 11 ISO and VirtIO drivers ISO under CD/DVD.
Hard drive bus set to SCSI with 60GB or 64GB.
Eventually, I noticed the “Press any key to boot from CD or DVD…” prompt flashed for a fraction of a second before the UEFI error. I kept missing it and letting it timeout. Once I caught it and pressed a key fast enough, the Windows 11 installer launched successfully. All previous errors were just because I wasn’t actually booting the installer.
After wasting so much time testing drive sizes, tweaking settings, switching BIOS types, and trying to outsmart Proxmox, it was that simple. So if you get “BdsDe” boot failures or your Windows VM won’t boot from ISO, make sure you’re not ignoring the “Press any key” prompt like I did.
Trevor, my second instructor at MTECH, helped me with this. When the installer finally worked, I thought, I need two VMs, and if I can’t recreate this, I’m stuck. I deleted the VM and started fresh to reproduce errors for Trevor.
He kept suggesting starting fresh, and once I stepped away, he started the VM. Suddenly it worked. We reviewed every step from another guide online, sure we had solved the issue. We agreed to document every detail. Trevor suggested deleting that VM too since it worked now, and I reluctantly agreed.
We recreated the VM but it still didn’t work for about another half hour.
From there went BROWSE >

I selected the drive that had VIRTIO-WIN-0.1.271 loaded in >I selected VIOSTOR >

Selected W11 >

AMD64 > pressed OK >
Selected RED HAT VIRTIO SCSI CONTROLLER > pressed INSTALL >
selected the available disk in the case of whichever VM I was making (this is a different one) > pressed NEXT >

From there, the installation proceeded normally. I thought it was weird the drive didn’t show up immediately like before, but it worked. Since drive space was tight, I decided to recreate the first VM rather than jump straight to the second one. For safety, I kept the first VM Trevor and I made successfully—no way I wanted to lose that progress and be stuck again. After all, I needed to keep moving forward.
However, when I tried making the second VM, I ran into the same issue: the drive wouldn’t show up at the window prompting me to select the install location. I repeated the process of loading the VirtIO driver but was confused—why hadn’t I needed to do this for the previous VMs?
After many failed attempts and Trevor also stumped, I researched online and found three differences in my setups:
-
The successful VM didn’t use QEMU Agent
-
It used VirtIO Block for the hard drive bus
-
I had set disk sizes at 64GB, then 60GB (which worked), because both Windows 11 VMs had to fit within Proxmox’s 125GB partition limit (about 12GB actually allocated per VM)
On my next attempt, I aimed for two VMs with only 30GB each, but after failing many times and retrying 60GB again, I stuck with 60GB.
Online resources clarified the issue: VirtIO Block requires the VIOSTOR driver to show the drive during installation, while SCSI requires VIOSCSI. I had been using SCSI without understanding this.
VirtIO Block is simpler and faster but needs VIOSTOR; SCSI is more flexible with advanced features and uses VIOSCSI.
When I recreated the VM following this knowledge, it worked. I don’t remember if I used VirtIO Block or SCSI in the end, but I suspect VirtIO Block with VIOSTOR since I knew where to find those drivers and didn’t see VIOSCSI drivers afterward.
Windows installed! I’m glad I kept that initial 60GB VM. Now I feel confident I know what’s needed to get Windows 11 installed on Proxmox VMs. Both VMs have 60GB disks, fitting within my 125GB limit. I don’t see a need for more VMs right now, so I’m sticking with these two and moving on.
Setting Up Windows 11 Enterprise VMs for Active Directory Domain Join on Windows Server 2025 (Proxmox Lab)
I’m building an Active Directory lab using Proxmox with:
What I’ve done so far:
-
Confirmed the domain controller VM is running and promoted to domain TESTLAB
-
Checked the domain controller’s IP address inside the server with ipconfig — it’s 192.168.50.191
-
Powered on the two Windows 11 VMs, named Win11Ent-1 and Win11Ent-2
-
Noted their IPs: 192.168.50.51 and 192.168.50.106 respectively
-
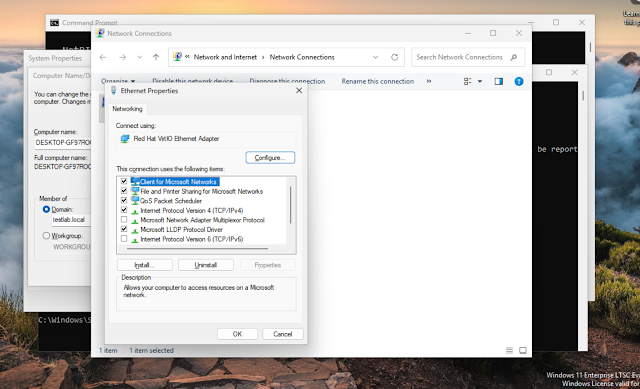
Changed the DNS server on both Windows 11 VMs to point to the domain controller’s IP 192.168.50.191 by:
Pressing Win + R, typing ncpa.cpl, pressing Enter
Right-clicking Ethernet adapter > Properties
Selecting Internet Protocol Version 4 (TCP/IPv4) > Properties
Setting Preferred DNS server to 192.168.50.191 > OK > Close
-
Verified network connectivity between the clients and server (e.g., ping, nslookup)
-
Preparing to join the Windows 11 VMs to the TESTLAB domain next.
This has been Truncat3d 00000000111100010100110______________end of line